57 KiB
Index
History of changes
| Date | Pages | Description |
|---|---|---|
| 2023-10-10 | Page 1-41 | Changed the name of the acronym of the project to Fediversity |
| 2023-10-10 | Page 5 | added a paragraph on the use of open hardware |
| 2023-10-10 | Page 11 | added two paragraphs on the selection of different NGI technologies |
| 2023-10-10 | Page 29 | added more elaborate justification of the purchase costs |
| 2023-10-10 | Page 34 | updated list of activities and costs eligible for funding |
| 2023-10-12 | Page 14 | Updated security measures periodic checking |
| 2023-10-12 | Page 21 | Added APELL to the identified partners list. |
| 2023-10-12 | Page 41 | Updated Gant Chart |
| 2023-10-12 | Page 3 | Added Open Source, Open Standards, Open Dependencies |
| 2023-10-12 | Page 15 | Added work package interdependencies and added a new page |
| 2025-06-12 | Page 1-26 | Added architecture document, rewrote to better emphasize data portability goal, increase supported applications |
Preamble
Let's make the internet once again a place where innovation empowers people and organisations while respecting their autonomy.
Fediversity offers portable open-source managed applications for online services, bridging gaps between their use, development, setup, integration and systems administration. The project will lay the groundwork for this in the form of documented reproducible deployment configurations. This way we make it easier to run public infrastructure.
Open Source, Open Standards, Open Dependencies
All software used, produced or needed by our project and it's outcomes will be licensed under a valid Open Source Software license, will not be encumbered by patents unless covered under the Open Invention Network and will not use API's or services that are not reproducible in a fully free manner.
No software specific for or usable by any single organisation will be created or produced under this grant.
Objectives and ambition
Objectives
Fediversity: Privacy-friendly, sustainable, transparent fair.
The Open Internet Discourse Foundation's project Fediversity is an effort to bring individuals and institutions easy-to-use, portable digital services with personal freedom at their core. We want to help provide everyone with high-quality, secure IT systems for everyday use. Without tracking, without exploitation, in a way that makes sustainable use of the world.
The goal of this project is offer an alternative to centralised online services and companies that operate closed ecosystems, thus creating a major impact on the future of the internet, our societies and economies — a unique and meaningful contribution to the Next Generation Internet initiative. This objective aligns with the work programme topic by advancing the development of alternative digital solutions that are more user-centric and transparent.
The key technical aspect of Fediversity is to provide the framework for networked applications to easily migrate between different hosting providers, or to their own infrastructure, while retaining full control over user data. This objective is important as it promotes technological sovereignity and choice, and offers an alternative to locking users into a particular platform or service. It would be a unique feature beyond what is currently available on the market.
Concretely, we aim to achieve the following objectives1:
- Implement a way to run online services emphasising user autonomy and data portability;
- Disseminate our results by engaging the open-source community to further expand on work in this direction;
- Exploit our work by enabling reproducible deployments of an initial set of portable applications.
In addition, the team will ensure that all parts of our services use open-source software. This will promote transparency and gives users the freedom to use, modify, and distribute the software as they see fit, without artificial restrictions or limitations.
Relevance
This proposal is highly relevant to the Horizon Europe programme, specifically to the Next Generation Internet fund. The objective of this topic is to support research and innovation in creating a more human-centric internet that prioritises user privacy, security, and control, while also promoting the ethical use of technology. The proposed work aligns with this objective by show-casing a way to run digital services that prioritises user control and data protection, and by using open-source software to promote transparency and ethical use.
Measurability
Tests will concisely describe the abilities the Fediversity system provides. These tests can be run on any sufficiently powerful machine with Nix installed, and reliably validate that the use cases work as intended. The proposed work is realistically achievable.
Methodology challenges
One of the challenges we have identified is ensuring the security and privacy of our users' data, even if we will not collect this directly. To overcome this challenge, we will use industry-standard open-source encryption methods and regularly update our software and hardware solutions to stay ahead of potential threats. We will also need to work with experts in data privacy and cybersecurity to ensure that our software is secure and protect user data. Before having the software enter production, a periodic security check (monthly or bi-monthly) will be held to verify required security measures have been taken and to check if any updates are needed. Where and if possible, we will automate these checks and integrate them in a 24/7 monitoring system.
Another challenge is that some of the software we aim to build upon is still somewhat new and as a result may still change more frequently. In order to deal with this, we will have to keep up with potential changes and at the same time provide a stable and predictable experience to our users.
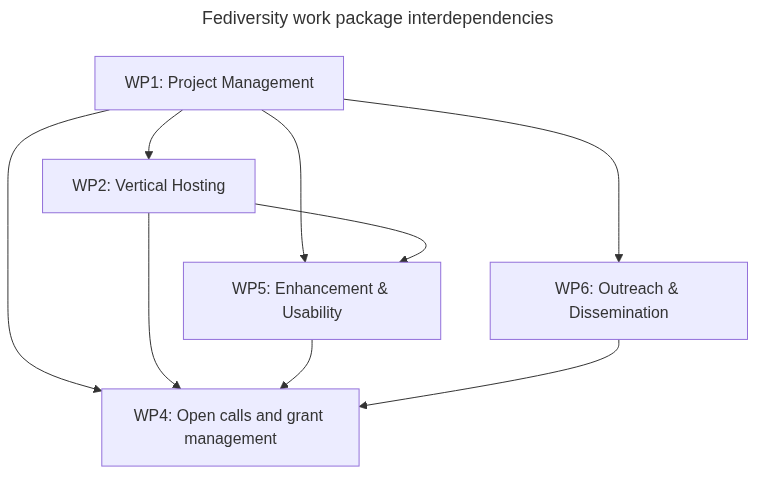
Work package interdependencies
To give a clear view of what interdepencies we expect:
- Project Management: will keep an overview of all other Work Packages.
- Vertical Hosting: will offer a 'feedback loop' and feed to WP5
- Vertical Public Organisations: (dropped)
- Open calls and grant management: will feed back to the vertical and feed to WP5
- Enhancement & Usability: will feed back to the verticals and feed to WP5
- Outreach & Dissemination
This diagram graphically represents the relations:
Impact
Project's pathways towards impact
Target groups:
- Hosting companies looking to offer open-source applications.
- Developers looking to expand on the available applications respecting user autonomy.
Societal outcomes:
- Give companies and organizations that specialize in web hosting a better starting point in offering such applications.
- The proposed platform could contribute to the creation of a more open and democratic digital landscape, where users have more control over their data and online interactions.
- The platform's focus on privacy and data portability could lead to greater trust in open-source digital platforms, which in turn could lead to increased participation and innovation.
Technological outcomes:
- Establish a better understanding of how to implement, maintain and run open-source managed applications respecting user autonomy.
- An increase in solutions around autonomous managed applications as well as in number of software packages supported by such solutions.
- Increased engagement with and innovation around open-source software, stemming from lowered barriers toward their adoption.
Economic outcomes:
- An uptake in the number of open-source managed applications offered by web hosts, as it becomes easier to offer these.
- Reduction in cost of running applications that preserve users' control over their data.
- Increased adoption of privacy-respecting software, as it becomes easier to consume these through the above-mentioned hosts.
Some specific possible quantitative estimates include:
-
Developer engagement:
Given that making portable services the default will need more of the open-source community to engage on this issue, we may measure for example developer engagement in social channels, support channels, issue trackers, as well as code forge metrics such as bookmarks, forks, merge requests, and third-party projects building upon our work or citing us as a source of inspiration.
-
User adoption:
If our project is successful in providing a user-friendly and privacy-focused platform for digital autonomy, it could attract a significant number of users.
-
Cost savings:
By promoting the use of open-source software and decentralised infrastructure, our project could lead to cost savings for public organisations.
-
Data portability:
The focus on data portability could have significant benefits for users, allowing them to easily switch between online platforms and take their data with them.
-
Market disruption:
If our project is successful, it could have far-reaching impacts. For example, if our software gains a significant share of the market, it could lead to more competition among online software services, potentially leading to improved user privacy and better options for data management.
There are several requirements and potential barriers that may determine whether the desired outcomes and impacts of the project are achieved. Some of them are:
-
Technical challenges:
As seen in our technology section, our project encompasses bridging numerous existing software packages, meaning project success depends on successfully integrating these.
-
Funding and resources:
The project will require adequate funding and resources to achieve its desired outcomes and impacts. The project team will need to secure sufficient funding and resources to cover the costs of software development, partnerships, and promotion. Failure to secure adequate funding and resources may limit the project's ability to achieve its desired outcomes and impacts.
-
Competition:
The project will face competition from other digital service offerings, including properietary ones and offerings oriented at self-hosting open-source projects. The project team will need to differentiate the platform and demonstrate its unique features and benefits. Failure to differentiate the platform from its competitors may limit the project's ability to achieve its desired outcomes and impacts.
Measures to maximise impact - Dissemination, exploitation and communication
Dissemination
We've identified multiple dissemination measures we can apply to our project in our plan to engage the open-source community to further expand on work in this direction:
-
Offering automated dev-ops workflows.
-
Ensuring external developers empowered to contribute:
We want for external developers to feel empowered similar to core developers, which we aim to achieve using accessible documentation, reproducible project infrastructure, tests doubling as live documentation of our components, a module upstreamed to nixpkgs, as well as by offering a familiar interface by making our core abstraction a NixOS configuration.
-
Developing key messages:
We'll develop clear, concise, and compelling messaging that highlight the benefits and unique features of our project, such as the focus on user control, data protection, and service portability.
-
Using multiple channels:
We will be utilising a variety of channels to reach our target audiences outlined above, among which through online communities, social media, webinars, blog posts, tech conferences and press releases.
Concrete examples of dissemination activities for our project will include:
- Properly document our work, so that potentials users may more easily understand when and how they might use it, whether directly or tweaked to their particular use-case.
- Maintain and highlight instant messaging channels where developers might ask questions and discuss potential improvements to the software.
- Creating a comprehensive user guide and knowledge base that provides detailed instructions and answers to common questions about the software, and making this guide available on the platform's website and social media channels.
- Hosting a webinar series that showcases the features and functionalities of our software, and provides tips and best practices for using it effectively.
- Participating in relevant conferences and events to raise awareness of our project and engage with potential users and partners, such as those focused on Nix, and showcasing our software in demos and presentations. These will include developer events such as NixCon, FOSDEM and CCC Congress to inform a diverse audience of the benefits of our stack and the other NGI technology solutions we are promoting.
Communication
Our communication strategies are already partially integrated in the dissemination measure above, but we'll outline them more in depth.
There are several communication strategies and measures that we will utilise during the whole lifespan of the project:
-
Developing a project website:
A project website will serve as a central hub of information about our project. It will be used to share updates, news, publications, and other project-related information. The website will be designed to be accessible and user-friendly.
-
Using social media:
We will reach out to Fediverse channels (e.g. Mastodon, Pixelfed, Peertube and Owncast) as well as commercial social media platforms such as BlueSky, Threads, and LinkedIn to reach a wider audience and share project-related news and updates. Social media are used to engage with stakeholders and respond to their queries and feedback. While our values may be closer aligned with the open-source social media, we will also still have use for the commercial ones to spread our message initially.
Exploitation
Planned exploitation measures, primarily aimed at hosting organisations, include:
- Work on integrating the software in an open-source package based around the use-case of a hosting provider.
- Help document the integration as well as the original software to facilitate further work in this direction.
Project content and handling of intellectual property risks
NGI as a whole operates according to open source principles and unencumbered (royalty-free) licensing, to ensure broad and lasting impact. The societal benefit of the initiative lies in the collaborative development of technology as commons. This democratises development and creates a level playing field for all. The vision of the NGI initiative, embraces the mantra 'public money, public code'.
IPR directly produced by the consortium — The Fediversity consortium consists of mature 'open' organisations, for which publishing all knowledge as reusable open content and free access publications is the norm. We offer all our own outcomes as a no-cost download, without any user tracking. Any scientific publication will be published either 'gold level' or 'green level' open access.
Project level IPR — Ownership of all (third party) project content and IPR developed through the Open Calls remains with the third parties executing technical R&D efforts. In order to ensure lasting impact, a clear open source IPR regime is therefore in place: all software, hardware and content funded through this programme should always be made available under a recognised libre/open license. Active and pending patents need to be explicitly declared in the application, proposals which have a direct and essential dependency on non-defensive patents are not eligible for grants NDAs are not acceptable.
We follow the Reuse.Software specification, which is the leading set of best practices on copyright handling. We will actively support our projects with achieving copyright compliance, as an unclear licensing situations significantly hampers uptake. Through the NGI0 review project (also ran by NLnet Foundation) we will advise and help people to set up proper IPR governance for their projects, including trademarks.
Work in most standards setting organisations is automatically covered by a strict IPR policy, requiring full declaration — which is typically followed by an effort to work around any patents in order to create a FOSS-friendly, unencumbered standard.
Handling the threat of software patents
The fact that patented technologies are out of scope for our research, does not mean that patents have ceased to be, and no longer pose a threat. Our projects work out in the open, and so groundbreaking ideas can be appropriated easily. We are mindful of the threat of so called 'patent trolls' or 'Non-Practising Entities' - especially since the amount of utility patent applications continues to rise. Last year, tens of thousands of patents on basic technologies like data processing were issued, according to the Patent Quality Initiative. It is in the interest of the entire community to help new ideas that come up to be protected against software patent threats.
Through NLnet we partner with several key stakeholders in the intellectual property community to make sure that we handle these threats in the best possible way. Through so called technical disclosure commons, which are endorsed by the USPTO as an IP rights management tool, derivative patent hijacking can be prevented. Defensive publications are documents that provide descriptions and artwork of a product, device or method so that it enters the public domain and becomes time-stamped "prior art".
This powerful preemptive disclosure prevents malicious parties from obtaining a patent on the product, device or method. In collaboration with our partners Open Invention Network, defensivepublications.org and LOT we intend to make sure that there are no patent hijacks along the way. We will integrate that aspect into the high level process on a best effort basis.
Summary
| Specific needs: What are the specific needs that triggered this project? | Expected results: What does Fediversity expect to generate by the end of the project? | Communication and dissemination measures: What dissemination, exploitation and communication measures will Fediversity apply to the results? |
|---|---|---|
| Gap between supply and demand of software: whereas a lot of open-source server-based software exists, adoption of open-source options appears to be lagging behind, in part due to the maintenance overhead that comes with traditional self-hosting and requires more technical know-how. | Easier and predictable use of NGI-supported open source software: We aim to provide hosting providers with a cookbook/script that will allow them to implement, and maintain NGI-supported open source software in such a way that it feels comfortable for IT staff to do. | Outreach towards main-stream consumers: Press and guerrilla marketing, tech talks and webinars, social media, project speaker bureau. |
| Use of open-source software is hard: The general misconception is that the use of open source software is hard and it is difficult for large organisations (both public and private) to run, and maintain open source software. | Rise in adoption of open-source given low-maintenance options: Given our initial offering of easily set up open-source server applications in our pilot with hosting organizations, we expect to see adoption of this software among end-users, hopefully creating a 'network effect' in these ecosystems. | Engage with technical, operational community and decision makers: Webinars for 'families' of projects to showcase progress to internet service providers, research networks, operator groups, hosters, CERTs, etc. |
| Service portability is lacking: Even though there are now regulations that state that you can get all your personal data from service providers. It is still quite hard to move from one platform to another. With the event of federated networks you can export your data from one instance and move to another. This is not easy and requires quite some work. | Basic level of service portability: We expect to get several projects to create a way to actually export both data and settings so you can not only move to another service provider, but also do so transparantly. | Make project results discoverable: One stop shop portal to browse through different categories of projects and discover new technologies of interest. |
| Engage European SMEs and investors: Create a competitive alternative economy based on open source with convenience and value-add services. |
| Target groups: Who will use or further up-take the results of the project? Who will benefit from the results of the project? | Outcomes: What change does Fediversity expect to see after successful dissemination and exploitation of project results to the target groups? | Impacts: What are the expected wider scientific, economic and societal effects of the projects contributing to the expected impacts outlined in the respective destination in the work programme? |
|---|---|---|
| Software and hardware companies and in-house developers: Developers (also in-house) from public and private sector that benefit from quality reusable components and turnkey best practices. | Significant uptake by interested users: Projects improve the state of the art and can be customised, offering distinct advantages over existing (proprietary or legacy) tools. | Societal: Sustainable ecosystem around open source and open hardware projects which creates a virtuous cycle of collaboration, growth and innovation. |
| Regular end users: Many technologies within NGI Zero directly benefit those that want to increase their online privacy, independence and security. | Adoption by service providers, network operators and platforms: Efforts within the infrastructure and hosting layer, and at the level of platforms and distributions will 'automatically' benefit users. | Societal: Privacy and security improvements help users avoid risks, especially important for vulnerable groups like minorities, whistle-blowers, activists, refugees and journalists. |
| Enterprises and public sector: Organisations can replace proprietary, possibly unethical business software with open source, user-respecting solutions. | Integration of project output into major open source solutions: Superior solutions tend to gradually replace legacy technologies and improving standards has a strong effect on the overall marketplace. | Economic: ISPs, hosters, network operators, companies and civil society (re)use project output to deliver services that grant users more autonomy and privacy. |
| Academia and research: Unlike proprietary ("black box") tools and services, open source solutions are well-suited for academics and private and public sector research as a subject and to experiment with new ideas. | Usage and (paid) services for enterprises and organisations: On top of state of the art FOSS solutions everyone can build competitive business and services. | Economic: We expect a new economy will start to evolve based on value added support and services for e.g. end-to-end communication, private data storage, federated and decentralised identity management. |
Implementation and planning
See the split-out architecture document.
Work plan and resources
Table 3.1g: Subcontracting costs
Not applicable?
Table 3.1h: Purchase costs
| Description | Category | Cost (€) | Justification |
|---|---|---|---|
| Test hardware | Other goods, works and services | 200.000 | For our UX research we need to acquire a reasonable diverse set of tablets, PC's and mobile phones so that we can support actually used devices. This is essential to deliver the kind of support people expect from software in general, but cloud services (like our social networking products from the NGI technologies we choose). We want to create a test lab that is also accessible to the chosen technology developers at request. We will at least need to acquire the latest new models of popular phones and tablets other devices every 3 months (estimated total of 60 devices by the end of the project) and new models of laptops, chromebooks and the likes every 6 months (estimated total of 30 devices by the end of the project) and a few PC’s with various form-factors and operating systems (estimated total of 24 devices by the end of the project). We expect to be using about 50.000 of the budget for this. Another substantial part will be used for a test-setup 'at scale' for running the actual services: server-hardware, networking-hardware, storage-systems. Also we need to account for hosting and networking-costs in dual locations. We will acquire about 80 server-systems, 12 storage-systems, and some networking equipment housed in two locations. All hardware will be second-hand as to keep cost low. For this we expect to be using about 130.000 of the budget. The remaining 20.000 euro we want to spend on two or four openhardware servers based on OpenPower to run a small pilot as part of the test/development setup to see where it makes sense to use OpenHardware in the setup for running Fediverse software. |
| Remaining purchase costs | 10.000 | Is for promotion and marketing material like stickers, banners, and other promotional material to hand out on each and every event we will visit. | |
| Travel and subsistence | 15.000 | Will be used for traveling between the Netherlands, the Nordics, France and the rest of Europe for attending conferences and other meetups. | |
| Total | 225.000 |
Table 3.1.i: Other costs categories
Not applicable.
Table 3.1.j: 'In-kind contributions' provided by third parties
Not applicable.
Capacity of participants and consortium as a whole
Fediversity is a unique collaboration of not-for-profit internet expert organisations with a strong track record:
NLnet Foundation (NLnet — NL) ~ Widely recognised as one of the leading grantmakers in the realm of internet and open technology. Introduced the internet in Europe in the eighties, and led the project that defined the vision of the NGI initiative. Now is the driving force behind NGI Zero, and responsible for over half of the active projects inside NGI.
ProcoliX ~ Web host dating back to the early stages of the internet. Today hosting public services like the NLUUG FTP server, one of the largest repositories of Open Source software in Europe and sites like Mastodon.nl and Petities.nl for the public good. Has a 'open source only' approach to running Internet IT Infrastructure.
NORDUnet ~ NORDUnet is an international collaboration between the National research and education networks in the Nordic countries. NORDUnet interconnects the Nordic national research and education networks and connects them to the worldwide network for research and education and to the general purpose Internet. NORDUnet provides its services by a combination of leased lines and Internet services provided by other international operators. NORDUnet has peering in multiple important internet exchange sites outside the Nordics, such as Amsterdam, Chicago, Frankfurt, London, Miami and New York.
Ethics self-assessment
Human embryonic stem cells and human embryos
- Does this activity involve Human Embryonic Stem Cells (hESCs)? NO
- Does this activity involve the use of human embryos? NO
- Does your activity involve the use of other human embryonic or foetal tisses/cells? NO
Humans
- Does your activity involve human participants? NO
- Does your activity involve interventions (physical also including imaging technology, behavioural treatments, tracking and tracing, etc.) on the study participants?' NO
- Does this activity involve conducting a clinical study as defined by the Clinical Trial Regulation (EU 536/2014)? (using pharmaceuticals, biologicals, radiopharmaceuticals, or advanced therapy medicinal products) NO
Human cells / tissues
- Does your activity involve the use of human cells or tissues (other than those covered by section 1)? NO
Personal data
- Does this activity involve processing of personal data? NO
- Does this activity involve further processing of previously collected personal data (including use of preexisting data sets or sources, merging existing data sets)? NO
- Is it planned to export personal data from the EU to non-EU countries? NO
- Is it planned to import personal data from non-EU countries into the EU or from a non-EU country to another non-EU country? NO
- Does this activity involve the processing of personal data related to criminal convictions or offences? NO
Animals
- Does this activity involve animals? NO
Non-EU countries
- Will some of the activities be carried out in non-EU countries? YES (potentially)
*Specify the countries involved*: The countries from which beneficiaries operate are not yet known (open call involving financial support to third parties). - In case non-EU countries are involved, do the activities undertaken in these countries raise potential ethics issues? NO
- Is it planned to use local resources (e.g. animal and/or human tissue samples, genetic material, live animals, human remains, materials of historical value, endangered fauna or flora samples, etc.)? NO
- Is it planned to import any material (other than data) from non-EU countries into the EU or from a non-EU country to another non-EU country?
(For data imports, see section 4.
For imports of human cells or tissues, see section 3.) NO
Is it planned to export any material (other than data) from the EU to non-EU countries? For data exports, see section 4. NO - Does this activity involves low and/or lower-middle income countries? (if yes, detail the benefit-sharing actions planned in the self-assessment) NO
- Could the situation in the country put the individuals taking part in the activity at risk? NO
Environment & health and safety
- Does this activity involve the use of substances or processes (or technologies) that may cause harm to the environment, to animals or plants (during the implementation of the activity or further to the use of the results, as a possible impact)? NO
- Does this activity deal with endangered fauna and/or flora / protected areas? NO
- Does this activity involve the use of substances or processes (or technologies) that may cause harm to humans, including those performing the activity (during the implementation of the activity or further to the use of the results, or the deployment of the technology as a possible impact)? NO
Artificial intelligence
- Does this activity involve the development, deployment and/or use of Artificial Intelligence-based systems? NO\
Other ethics issues
- Are there any other ethics issues that should be taken into consideration? NO
[x] I confirm that I have taken into account all ethics issues above and that, if any ethics issues apply, I will complete the ethics self-assessment as described in the guidance 'How to complete your Ethics Self-Assessment'. (See Guide 4 section 5)
Financial support to third parties in Fediversity
Financial support in the form of a grant awarded after a call for proposals
As detailed in Part B, Fediversity in addition to pursuing its goals directly, will further contribute 15% of its budget to the development of related digital commons through financial support in the form of grants awarded to third parties through bi-monthly open calls for proposals.
In this annex we describe the following aspects of this financial support by detailing our approach to managing a dedicated fund supporting a series of open calls related to Fediversity:
- Objectives and results obtained of third party financial support
- Specifications of third party financial support
- List of activities and costs eligible for funding
- Definition of persons or categories of persons which may receive financial support
- Criteria for awarding financial support
- Criteria for calculating the exact amount of the financial support
Objectives and results obtained of third party financial support
The core objective of the grant component of the Fediversity programme is to fund and support independent researchers and developers and organisations that contribute open source technology for a more open, trustworthy internet pertinent to the NGI technologies further developed within Fediversity.
The way we do this is a tailormade version of the open call grant mechanism which — through acclaimed programmes like NGI Zero and NGI Assure — has already been responsible for most of the projects within NGI: the open call operated by NLnet foundation.
NLnet is the oldest internet technology grantmaker in Europe, and has decades of track record in funding strategic efforts. We will open a dedicated fund for the calls from the Fediversity Pilot.
As a recognised public benefit organisation NLnet operates transparently, is publicly accountable and the goals of the topic in the Work Programme align with its statutory mission. Any grants that will be handed out to individuals, companies, NGO's or other types of legal entities are donations that fall under the most beneficial tax conditions as 'philanthropic gifts'.
The results of the Fediversity grant programme consist of new or improved digital commons that have a clear link to its research topics and contribute to the public benefit. These characteristics are requirements for projects to be selected and funded, and stem from the overal vision that underpins the Next Generation Internet initiative.
Specifications of third party financial support
We will competitively award 450 000 EUR worth of grants to third parties. This is 15% of the Fediversity budget. Fueling great R&D is the core objective of this Innovation Action. We have detailed the list of activities that qualify for financial support, the entire procedure, the results to be obtained, who is eligible, the competitive criteria for awarding financial support, and the criteria for calculating the exact amount of the financial support (competitive, best value delivered) below.
List of activities and costs eligible for funding
The following types of activities qualify for financial support, provided they are cost effective and have a clear link to the topics directly relevant to Fediversity and the objectives set out in the work programme/call:
- Primary ring: Fediversity makes intensive use of NixOS for the hosting stack. Projects that improve, enhance or add to this stack.
- Secondary ring: applications that can be added to the Fediversity stack.
- Tertiary ring: tools or applications that enable provisioning, monitoring, authentication, etc. for the Fediversity stack.
- Understanding user requirements and improving usability/inclusive design.
- Necessary measures in support of (broad)er deployability, e.g. packaging.
- Participation in technical, developer and community events like hackathons, IETF, W3C, RIPE meetings, FOSDEM, etc. (admission fee, travel and subsistence costs).
- Other activities that are relevant to adhering to robust software development and deployment practices.
- Project management.
- Out-of-pocket costs for infrastructure essential to achieving the above.
Definition of persons or categories of persons which may receive financial support
There are no categorical exclusions of persons who may not receive support from Fediversity.
Given equal proposals, inhabitants of the EU and its associated countries are given priority, however if the project is of exceptional quality and the proposer holds unique technical expertise proposals from outside of those geographic areas can be eligible as well.
Young people that have not yet reached the age of legal consent in their country of origin (typically 18 years old) on the date of the deadline may apply without any constraints; consent from a legal guardian such as a parent does not have to be provided prior to initial submission, but will be required to enter any further negotiations.
Special efforts are made to reach out to talent from under-represented parts of the community.
Criteria for awarding financial support
Projects are judged on their technical merits, strategic relevance to the Next Generation Internet and overall value for money. The key objective is to deliver potential break-through contributions to the open internet linked to the NGI technologies which are the topic of Fediversity. All scientific outcomes must be published as open access, and any software and hardware must be published under a recognised free and open source license in its entirety.
The proposed IPR regime is in line with the approach in other NGI programmes such as NGI Zero and is 100% compatible with the vision of the Next Generation Internet initiative. It ensures lasting impact and reusability of results.
Payment is upon delivery, which is fair. However, should during the executing of a project the beneficiaries face any major hardships without having a financial safety net — including being struck by natural disaster, serious personal medical crisis or other disruptive life events that prevent them from timely completion of the project and subsequent entitlement to a donation — they may upon providing proof of the circumstances be granted a proportional amount as hardship contribution.
First stage assessment
Based on the submitted proposals, projects receive a first check for eligibility in terms of alignment of goals and criteria with the sub-granting call. In this stage hard eligibility ("knock-out") criteria specific to the sub-granting call are checked. Project proposals are written in English and:
- should be in line with the NGI vision and the sub-granting call applied for
- should have research and development as their primary objective
- should satisfy any other hard eligibility criteria specific to the sub-granting call, such as geographic limitations
All projects that fail on any of these knock-out criteria, will not be further reviewed and will be marked ineligible. The rest of the projects will be given a score based on the proposal text as submitted.
Projects receive an initial rating on three criteria:
| Weight | Criterion |
|---|---|
| 30% | Technical excellence/feasibility |
| 40% | Relevance/Impact/Strategic potential |
| 30% | Cost effectiveness/Value for money |
The total weighted score of projects has to be above 5 (out of 7) to pass to the next stage.
The projects which are not taken into the second round are informed that their project is not selected, so that they may try to find funding elsewhere as soon as possible — or continue without additional funding (as happens a lot).
Second stage assessment
The second stage is used to select strategic projects which not only satisfy the minimal criteria, but also have potentially a lasting impact on society. Projects are to be selected based on their potential contribution to the Next Generation Internet and its key drivers for change. In the second stage, the reviewers are able to ask additional clarifying questions and make (minor) suggestions to improve the quality and impact of the project.
This typically involves questions such as:
- what is the difference in approach to existing projects U, V and W
- how will you approach complicating factor X
- can you back up or validate claim Y
- have you considered collaborating with complementary effort Z or using standard A
- the rate you have applied for task B is very high compared to the perceived value of that task. Can you explain, or would you like to reconsider?
- can you clarify how you intend to make the outcome of the project (self)sustainable
- how does upstream project D feel about your application
In addition, the review team will do independent verification of facts, methods and claims. If necessary they verify relevant information through their expert network. This is done without revealing personally identifiable information, unless there is explicit consent from the submitter that their project may be shared. The second stage typically lasts two-three weeks. If a project is unable to prepare all the answers to the questions and/or a modified proposal within the allocated time frame, the project may be moved to the next round. Note that the proposed project budget may change during this phase due to added or deleted project milestones.
After the second stage is completed, new ratings are calculated based on the revised plan. If the revised plan scores lower than the original proposal, the original proposal is rated. Projects are subsequently ranked by the team according to the overall expected value and impact to the NGI initiative. A cut off point is determined, based on the overall quality of the round and the remaining budget. The projects that fall below the cut are (similar to the first round) informed that their project is not selected, so that they may try to find funding elsewhere as soon as possible - or continue without additional funding.
Third stage: Independent review committee
An independent review committee checks the final selection of projects. The review committee consists of independent experts from the internet and FOSS community, academia and the public sector. The committee receives no remuneration for its work, and its members have no other economic interests with NGI and/or links to NLnet Foundation as the grant-making organisation. Each project is reviewed for eligibility independently by at least two members of the review committee.
The outcome of the selection process is randomly divided among the members of the Review Committee. The committee validates that all the projects that are nominated are indeed eligible for funding, budgets are frugal, and that there are no other concerns. This creates a transparency trail with regards to eligibility and cost effectiveness of the proposed solutions, while retaining confidentiality of the preceding procedure. If a project fails to meet the criteria of the independent review committee, the concerns are sent to the proposer and the project is pushed back to the next available call. If there is no future call, the project is declined.
The external review board does not have to review amendments to an already granted project in case of:
- changes in the composition of the project team
- adjustments of a project plan without budget changes
- additional tasks within the same scope and using equivalent rates, as long as the total grant amount stays below 60k euro
Criteria for calculating the exact amount of the financial support
The call text stipulates that subgrants between 10k and 50k euro are the expected target range.
Our long term of experience with precisely this type of funding instrument has taught us that there is already benefit below this scale — and in fact being able to offer more modest amounts actually invites a different (but very interesting) group of contributors that would consider those higher amounts above their capacity. We therefore allow even smaller project to apply, setting the bandwidth for proposals between 5 000 and 50 000 euro. Obviously, this comes with additional overhead at our end — but we believe that to be worth it.
The amount to be granted to each third party should be the amount necessary to achieve the key objectives of the action. During the three stage review process, the overall 'value for money' and strategic potential of the proposal are part of the review, and thus of the ranking.
We have a rapid succession of project funding opportunities, so we can iterate and grow talent instead of having a 'leap of faith' with a select few projects. Excellent teams that have successfully completed their project, can apply for additional funding again — provided that a higher amount is necessary and delivers enough additional value. They are judged along the same criteria as the rest of the people in the grant round they are entering.
Proposals must adhere to the following boundary conditions:
- a single proposal MAY request a grant allocation up to 50k euro.
- a significant part of the work within a project MUST have been successfully completed before an amendment to the project or a new propoposal from the same applicant can be awarded: this means that the project deliverables have been made publicly available under recognised open/free licenses, that any software artefacts delivered were WCAG compliant, and that the outcomes of any third party audit have been satisfactorily dealt with.
- If a grantee seeks an amendment or new grant, the outcomes of the previously delivered work are taken into account during the evaluation.
The exact amount of financial support is determined by NLnet based on the projected cost and estimated value of the proposition. Any proposed amount is to be adjusted for costs that are deemed ineligible (see above) as well as for the cost of any additional activities recommended by NLnet. The final amount is established in the memorandum of understanding between NLnet and the grantee. If the grantee does not agree with the size of the grant offered, they may decline and withdraw the proposal prior to signing the MoU at any time.
NLnet as the grant handling organisation is a recognised public benefit organisation, and the goals of NGI are within its statutory mission. Any grants that will be handed out, to individuals, companies, NGOs or other types of legal entities are donations that fall under the most beneficial tax conditions as 'charitable gifts'.
Maximum amount to be granted to each third party
The maximum amount to be granted per third party over the lifetime of Fediversity is 60k euro. A third party can be a formal organisation (of any type) or an individual.
Confidentiality and privacy
We take confidentiality of information conveyed to us, and the privacy of our applicants and grantees very serious. We have minimised the amount of information requested during the application, and until the point where the actual grant process starts applicants can remain anonymous at their own discretion. In our privacy policy we inform potential applicants that they can use an alias and a temporary email address, and upon sharing a valid public OpenPGP key we will use OpenPGP to encrypt any further communication. As long as a project is not accepted, the applicants real identity is not relevant to us. If the proposal never goes beyond that phase they can remain anonymous.
In order to review and process project proposals we need to grant access to the professional staff of NLnet foundation responsible for reviewing and running the open calls associated with Fediversity (WP4). Since confidentiality is a critical aspect of the trust relationship we have with projects, at no point in time will proposals be shared with third parties without explicity permission, not even partners within Fediversity. Sometimes opportunities will arise outside of the context of this fund, or there is a potential to support the project in some other way. At the time of submitting the proposal applicants either grant NLnet Foundation the right to keep any information submitted on record — should future funding opportunities arise — or not. When the latter option is selected, NLnet will remove the information associated with the proposal if it is not successful. If they chose to allow NLnet to keep the information at hand, NLnet may at some point in the future bring them into contact with others at any given point in the future — but again only after explicit written consent from applicants.
When a project makes it through the first two stages of the selection process (see above), we need to share some information with the independent Review Committee — which consists of a small group of trusted experts. We do not pass on names of individuals (nor their contact details) onto the committee, but the committee members do receive and evaluate the granted proposal in a confidential manner.
When a proposal makes it through the third round and goes into the grantmaking process, we legally need to retain the applicants information for compliance purposes for at least seven years. We share contact details with our (not-for-profit) partner organisations in order so they may assist the projects with mentoring and technical advice.
NLnet is also the coordinator of NGI Zero Review, through which projects may receive complementary services e.g. accessibility audits, localisation support, packaging, security reviews etc. Supporting organisations within Fediversity do need to actually contact people in order to support or mentor them, NLnet will ask grantees to allow them to make contact information available to these partners — but we do not necessarily reveal their real identity. Applicants may provide us with an alias which will be what we expose to partners instead.
If people request a copy of their application, this is sent to the email address they themselves provide to use. We assume people have a good understanding of who has access to the associated mailbox and/or can observe their mail server traffic.
The European Commission and its appointed project review committees receive management information about projects receiving grants from these calls, but not the proposals themselves — and only the initials of the names (or aliases) of individuals are shared.
We ask people to inform us of any additional security and privacy constraints they have in our privacy policy, and we will try to accommodate such constraints to the best of our abilities — or tell them we are not able to do so. That at least gives people the choice to continue their interaction with us or not.
Conflict of interest resolution
The reviews within the Fediversity grant programme are done by full time professional staff of a recognised and professionally audited public benefit organisation with a significant track record (NLnet foundation), hired to perform impartial and objective project reviews without economic interest, political or national affinity. Every project is reviewed by multiple full time staff members, and independently from that all projects proposed for funding are again reviewed by multiple well-regarded experts from academia, the internet world and the public sector.
Institutional conflicts of interest
As the organisation responsible for performing the reviews within the Fediversity grant programme, NLnet foundation offers strong guarantees it does not in any way have any financial or other benefit from awarding certain proposals over others. Note that NLnet foundation is entirely independent, and has been so ever since it was founded in 1989. NLnet currently has no organisational ties with other legal entities — with the noted exception of its wholly owned fiscal fundraising entity Commons Caretakers, which for obvious reasons is excluded from requesting grants from the Fediversity grant programme. As part of managing its own financial endowment, NLnet has some small historical investments in SME companies and small investment funds. Companies financially invested in by NLnet are also explicitly excluded from receiving any grants through Fediversity.
Although they are not in any way involved with the review, the other legal entities that are part of the Fediversity consortium and their staff are also fully excluded from requesting and receiving grants through the Fediversity grant programme. This avoids conflicts of interest within the consortium, which was already minimal due to the fact that NLnet is also the coordinator.
Personal conflicts of interest
Reviews are performed by full time professional staff, hired to perform impartial and objective project reviews without economic interest, political or national affinity. For obvious reasons, NLnet staff are not allowed to have any financial or other personal benefit from grant proposals they are responsible for reviewing in any way either — other than the longer term public benefit. This allows them to fulfil their tasks in an impartial manner. The same holds for those people with which the reviewers have close family ties (spouse, domestic or non-domestic partner, child, sibling, parent etc.), and for any legal entities in which NLnet (or its staff) may hold stocks, shares or other economic rights.
Independent review committee
The standing review committee consisting of independent experts from the technical and academic internet community and the public sector validates the outcome of the selection procedure of each round on criteria of eligibility and budgetary efficiency. To ensure their independence, the members of the review committee are not attached to any of the consortium partners within Fediversity as employee, member of the board of directors or member of the board of supervisors.
Members of the independent review committee, their employers, their coworkers and their relatives are themselves excluded from submitting projects to the Fediversity grant programme.
Membership of reviewers in associations and not-for-profits
Note that the above explicitly does allow for past and present non-remunerated involvement of NLnet staff in not-for-profit legal entities serving the public interest, including those that were part of previously funded efforts within its funding programmes in which the partners were involved. This also includes paid and unpaid (board) membership of professional or ideological organisations such as ACM, IEEE, Internet Society, FSF, ICANN, OSI and Unix user groups, legal umbrellas such as The Commons Conservancy as well as open standards bodies like OASIS and W3C.
Submissions from those organisations (and other people involved with them) are not considered to constitute a conflict of interest. The 'reviewer paradox' is similar to the more classical 'observer paradox': in order to be able to properly review the relevance of proposed R&D at the cutting edge of technology, reviewers have to have a level of knowledge that only exists within the R&D ecosystem itself.
We believe it would not be proportional to exclude members of associations and volunteers within not-for-profits to exclude them from receiving support through the Fediversity grant programme, and we believe the ample additional quality assurances and third party checks made within the Fediversity grant programme allow for this sane approach.
Non-commercial constituencies
As mentioned before, all legal entities that are part of the Fediversity consortium and their paid staff are excluded from requesting and receiving grants through the Fediversity grant programme. This actively blocks any applications from the entire paid staff from the organisations within the consortium as well as the leadership involved with Fediversity: there is a 'Chinese wall' between the projects which are funded and the partners supporting the projects.
We believe it would not be proportional and in fact be undesirable to categorically exclude the membership and volunteer constituencies of the not-for-profit organisations within the NGI Zero ecosystem from grants. Besides NLnet foundation, neither of the partners is involved in any way with the actual review of projects and the resulting selection. The fact that people choose to contribute in an unpaid capacity to idealistic organisations that play an active and constructive role in e.g. the internet and open source ecosystems should not affect their ability to receive funding for a possible contribution. The same holds for (former and current) students and (former and non-remunerate) doctoral candidates of the academic partners in Fediversity. In fact, the ability to reach motivated and qualified people aligned with the core mission of NGI is one of the reasons these organisations were involved in the first place.
Given the clear and consistent separation between the rest of the consortium and the selection process, and the strong quality guarantees from the whole procedure, NLNet and the rest of the Fediversity consortium elected to place no restrictions on proposals from the non-commercial constituencies surrounding the consortium partners in Fediversity — with of course the noted exception of the grantmaking organisation (NLnet foundation). Consortium members have been instructed to stay clear from project proposals from their constituencies, and are aware that failing to keep adequate distance to proposals from their constituencies will disqualify the proposals involved.
Overview of project displayed in a Gantt chart
-
Disseminaton and exploitation of research results defines the terminology we use to frame our objectives. ↩︎